Category: cloud
-
-
InfoQ – January 2025
From Apache Hudi 1.0 to the latest controversies in the database world, from AWS Glue 5.0 to data transfer terminals, here are the articles I wrote for InfoQ in January 2025. Read the full article.
-
Around the World in 15 Buckets
Today, we’ll embark on a little journey around the world using S3. We’ll copy various objects across AWS regions worldwide, aiming to answer two simple questions: Does the storage class affect the speed? How does the size of the object influence the transfer time? Read the full article.
-
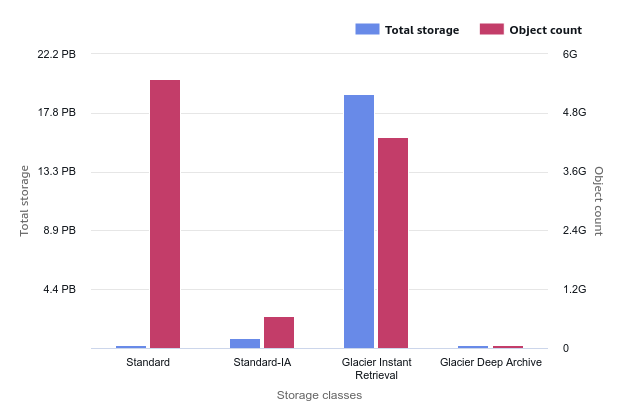
S3 Lifecycle or Intelligent-Tiering? Object Size Always Matters
Whenever you develop your logic with Lifecycle Rules or you delegate the logic to the S3 Intelligent-Tiering class, the average size of your objects on S3 is a significant factor in your storage costs. Read the full article.
-
AWS CN-UG Amarathon Geek Talk
I am glad to be part of the AWS CN-UG Amarathon Geek Talk, a 12-hour online event hosted by the CN-UG (AWS China User Group). My short talk will be about Amazon S3 and include a short journey around the world and cloud regions. Read the full article.
-
Designing Cloud Applications for Elasticity and Resilience
What is resilience by design? Why is elasticity important? In this 60-minute live roundtable, four expert panelists will explore the key concepts of elasticity and resilience from the perspective of cloud applications. Read the full article.
-
InfoQ – October 2024
From AWS Console-to-Code to Cloudflare Ephemeral IDs, from Valkey 8.0 to Amazon EC2 Graviton4 instances, the news I covered for InfoQ in October. Read the full article.